2020 CISCN 华东南赛区
web1
1 | zip -r is useful, and don't forget /var/www/html/***********/cat.php |
利用$msg = sprintf($msg, $value); 打印文件上传位置me0w_mE0w_miA0
访问me0w_mE0w_miA0/cat.php提示vim,拿到源码
cat.php
1 |
|
spl_autoload_register();没有任何参数的情况下调用spl_autoload();
class_name
file_extensions在默认情况下,本函数先将类名转换成小写,再在小写的类名后加上 .inc 或 .php 的扩展名作为文件名,然后在所有的包含路径(include paths)中检查是否存在该文件。
上传fffffffffffuck.inc
1 | <?php |
反序列化:O:13:"ffffffffffuck":0:[],将{}换为:[]虽然反序列化失败,但是还是调用了__wakeup
拿到flag:ciscn{keQXj78JHVUKjssqgD}
web2
提示source.php,composer
1 |
|
composer.json
1 | { |
hint给你excel.php的源码
1 |
|
file_get_contents在处理data:,xxxxxx时会直接取xxxxxx
而include会包含文件名为data:,xxxxxx的文件
但是我们无法直接创建data:的文件夹
先用./data:创建data:文件夹
再用data:来绕过if(!stripos(file_get_contents($f),'<?') && !stripos(file_get_contents($f),'php'))
web3
登录这边看这login.php构造一下符合正则规则的参数就好了,登了取下sessionid
然后qr.php里,sql注入明显的点,直接拼接的,$data来自于扫描二维码得到的数据,二维码里是个json:{"id":"xxxx"}。
1 | $sql="insert into record(p_id, userid)values ('".$data['id']."','".$user->getCardID()."');"; |
写盲注脚本爆破一下:
1 | import requests, time |
web4
1 | <?php |
拿到pass=ob_end_clean_is_surplus
文件上传与网上某题相近
exp.py
1 | SIZE_HEADER = b"\n\n#define width 1337\n#define height 1337\n\n" |
分别上传webshell.fuck,还有.htaccess拿到flag
web5
1 | ccopy_reg |
提权没环境复现
web6
1 | import requests |
web7
浏览一遍代码后发现一个弱类型比较
1 | function getUser() |
如果我们能令token以0e[0-9]+的格式的话,就可以绕过身份验证机制
而生成token的代码为:
1 | function setUser($username, $password) |
因为0e[0-9]+是在base64中的所以我们构造:username=%D1%EDv%EF%BE&password=%D7m%F8
至此获得admin权限
upload处有个任意文件上传,但是我们不知道admin的上传目录,我们不得不进行sql注入
notes.php处有个神奇的todo:
1 | if (isset($_POST['contents'])) { |
如果我们能控制$data->contents == $_POST[‘contents’],且可以控制$data->username出现引号逃出引号的包围,就可以进行sql注入了。
而我们的缓存的加密函数是:
1 | class CBCCrypt { |
其中$iv是受到我们控制的
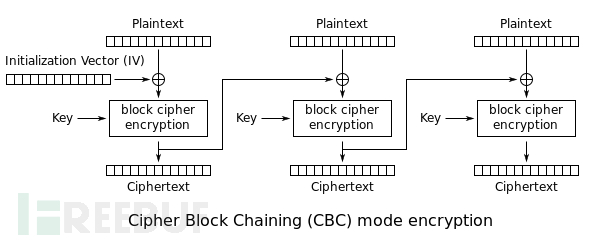
根据cbc加密的原理我们可以知道,通过修改iv从而修改初始的16个字符串
爆破合适iv的脚本:
1 |
|
1 | import requests |
上传名为file的文件,得到config/admin/secretpath/profile
结合include "config/${_SESSION['token']}/profile";从而getshell
token是base64编码,因此可以精心构造出admin/secretpath
由于没有题目环境便无法验证
web8
网络上找到了一个payload:http://igml.top/2020/08/21/2020-ciscn/
1 |
|